Authentications
Was this helpful?
Was this helpful?
Path: Client Management > Authentications
Defining the authentication method required for the API in the system can help users quickly identify the API type and functions when creating API groups; for example: Which APIs will be used for setting the authentication method of the online bank. This page can only query / add / modify / delete authentication methods, but APIs are not added from here.
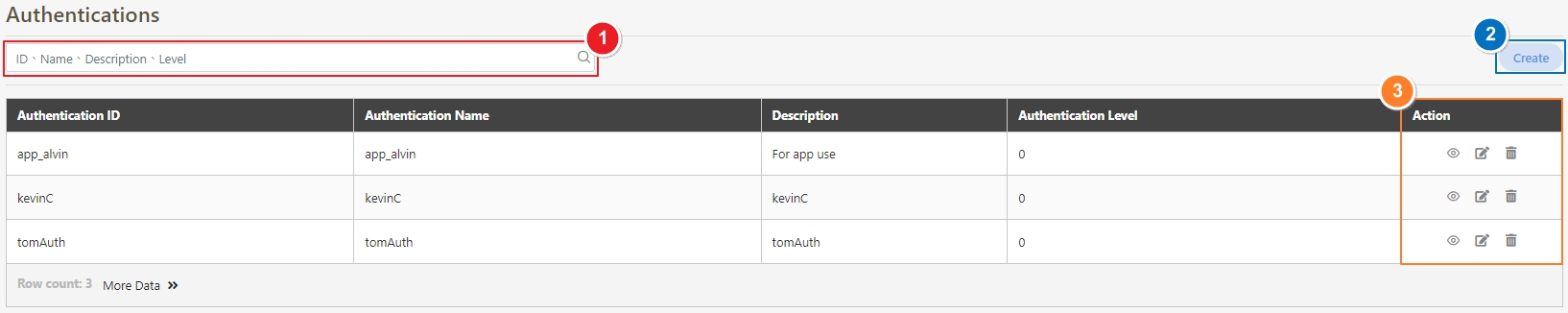
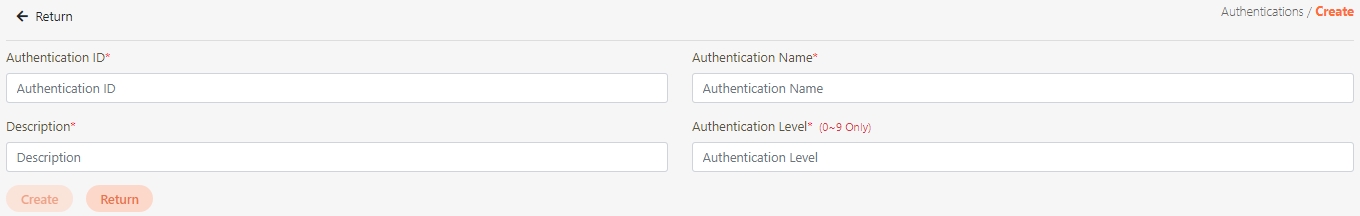
Click Create to access the authentication creation page.
Fill in the data or make selections as instructed below. The fields marked with “*” are required.
Authentication ID*: Code to identify the authentication; limited to alphanumeric characters, underscore (_) and hyphen (-).
Authentication Name*: Name that can identify the authentication.
Description*: Description of this authentication.
Authentication Level*: No implemented function in the system. It provides information to TSP, and when TSP implements (customer operation) the authentication, it will decide whether secondary authentication is required.
Click Create to save and exit.
To search for authentications, enter the keywords to search for related authentications.
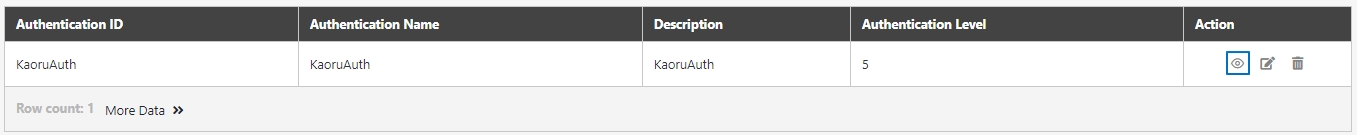
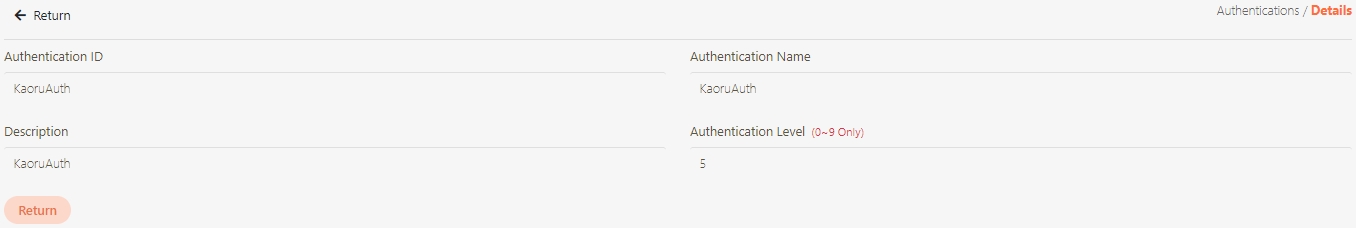
The information in Details can only be viewed and not edited.
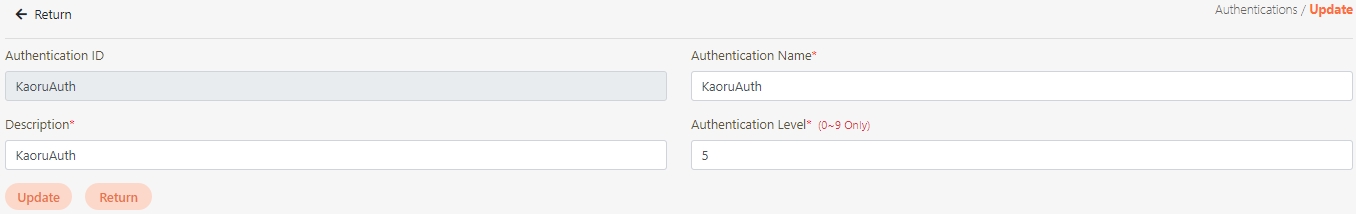
Modify the desired fields, and click Update to save and exit.
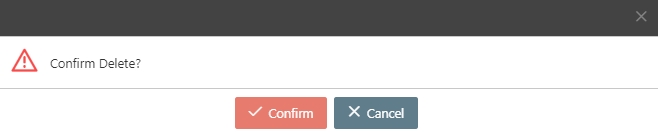
A warning prompt displaying the message “Confirm Delete?” will pop up. Click Confirm to delete the authentication and exit.
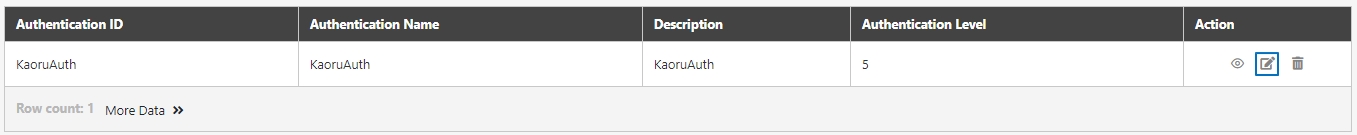
Search for the authentication to view details, and click on theicon to access the authentication details page.
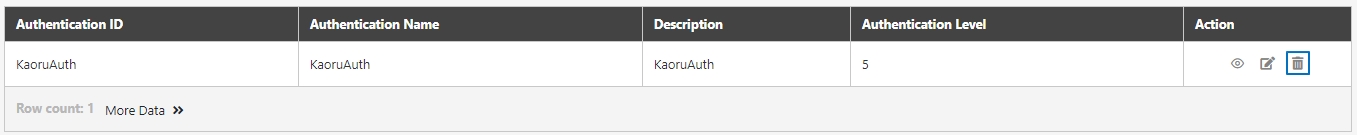
Search for the authentication to modify, and click on the icon to access the update page.
Search for the authentication to delete, and click on the icon to proceed.