Generating Certificate
keytool -genkey -alias example-comp -keystore example-comp.jks -keypass example-pwd123 -storepass example-pwd123 -keyalg RSA -keysize 2048 -validity 365 -v -dname "CN=www.example.com, OU=dgr, O=tpi, L=taipei, ST=taiwan, C=tw" -ext "SAN=DNS: www.example.com,IP:127.0.0.1"keytool -list -v -keystore example-comp.jks -storepass example-pwd123keytool -importkeystore -srckeystore example-comp.jks -destkeystore example-comp.p12 -srcstoretype jks -deststoretype pkcs12 -keypass example-pwd123 -storepass example-pwd123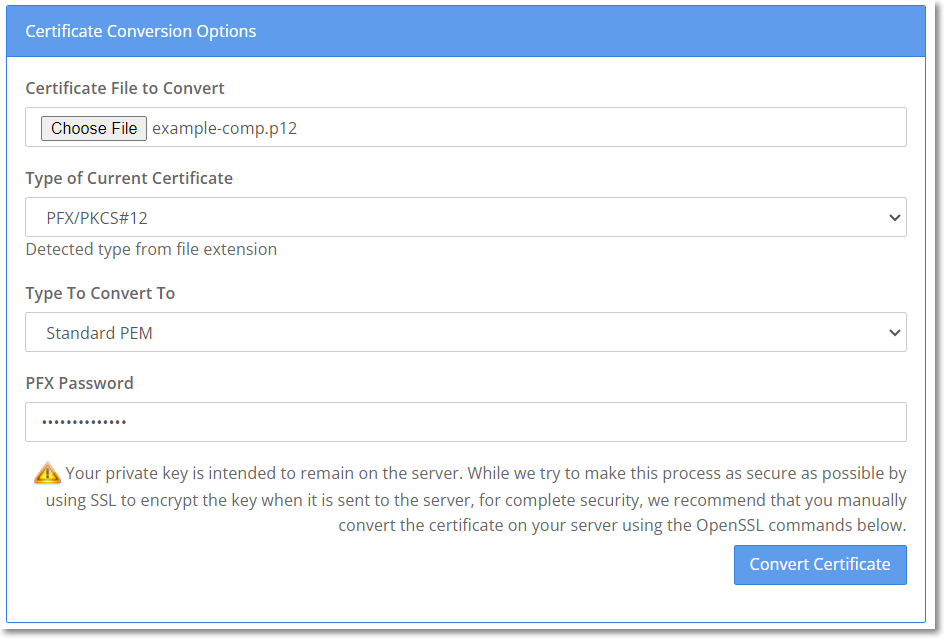
Was this helpful?
