GTW JDBC IdP
Path: Client Management > GTW JDBC IdP
In this section, you can find instructions on how to maintain the JDBC authentication servers using the gateway.
Search GTW JDBC IdP
To search for GTW JDBC IdP, you can search using the relevant information as keywords.
Client List of GTW JDBC IdP
To view the details of GTW JDBC IdP, you can search using the relevant information as keywords, and click on the
 icon to access the GTW JDBC IdP Client List page.
icon to access the GTW JDBC IdP Client List page.
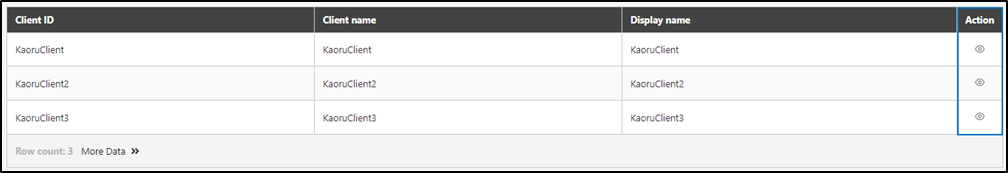
Users can create, update, view details, and delete the clients.
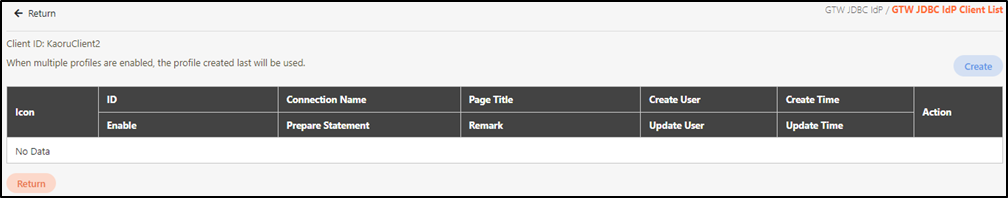
Create JDBC IdP Client
Click Create to access the JDBC IdP Client creation page.
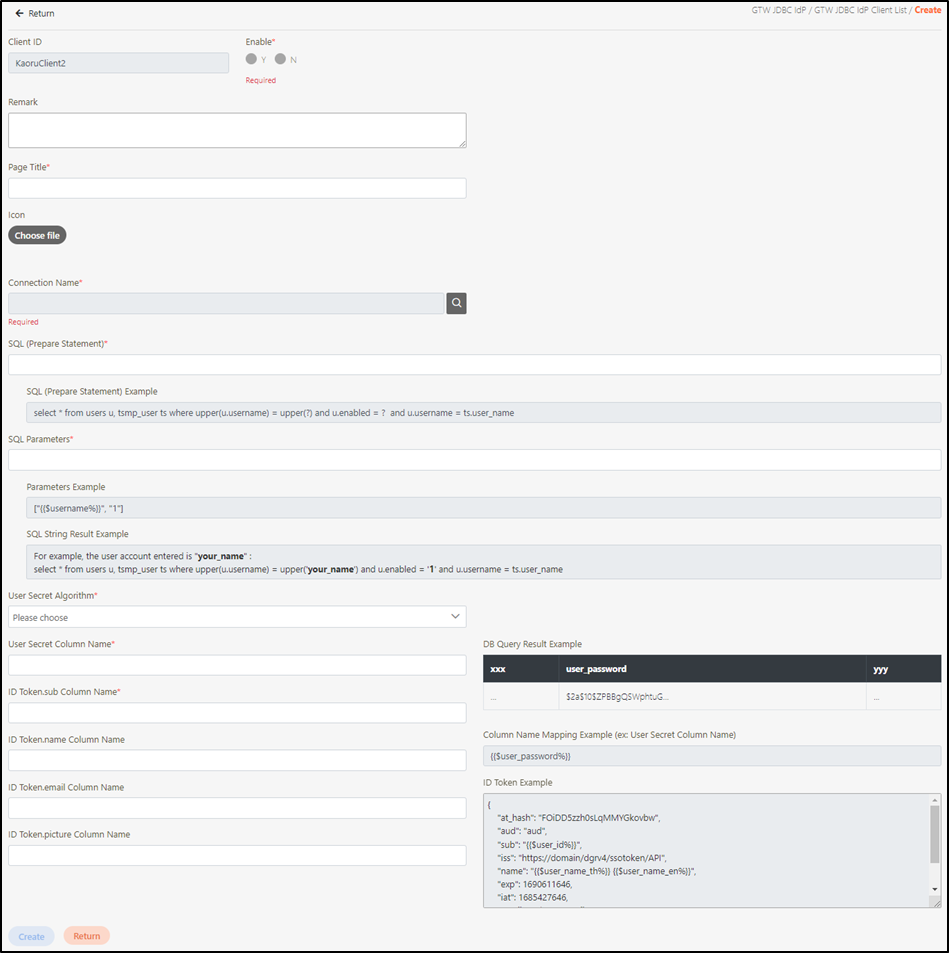
Fill in the data or make selections as instructed below. The fields marked with “*” are required.
Enable*: This account is active (Y) or inactive (N).
Page Title*: Header of the login page.
Icon: Click Choose file to select and upload an identifiable GTW JDBC IdP image. If no image is uploaded, the system will automatically use the digiRunner logo.
Connection Name*: The name of a database, network, or other resource connection for system identification and management. The Connection Name can be created in System Configs > RDB Connection.
SQL (Prepare Statement)*: A precompiled mechanism for SQL statements that improves both the security and performance of database operations. Commonly used for parameterized queries to prevent SQL injection attacks.
SQL Parameters*: Special placeholders used to pass values when executing SQL statements. These parameters help separate the statement structure from data, improving security, readability, and performance while effectively preventing SQL injection attacks.
User Secret Algorithm*: The algorithm used to encrypt or hash sensitive user data, such as passwords, to ensure data security during storage and transmission.
User Secret Column Name*: The column name in the database table used to store user passwords or other sensitive information, typically found in user account tables.
ID Token.sub Column Name*: The database column corresponding to the .sub field in the ID Token, representing the user's unique identifier for authentication and user identification.
ID Token.name Column Name: The database column corresponding to the .name field in the ID Token, typically used to store the user's full name or display name.
ID Token.email Column Name: The database column corresponding to the .email field in the ID Token, used to store the user's email address.
ID Token.picture Column Name: The database column corresponding to the .picture field in the ID Token, used to store the URL of the user's profile image.
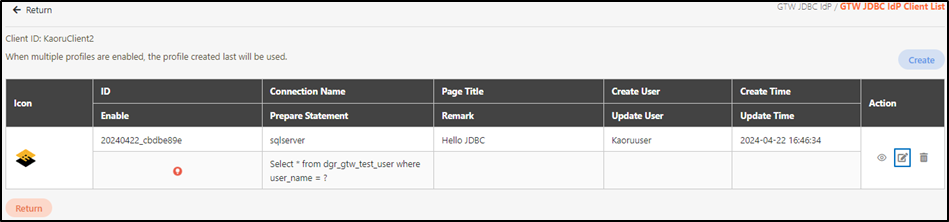
Manage JDBC IdP Client
To view the details of the JDBC IdP client, search for the client you want to view, and click on the
 icon.
icon.
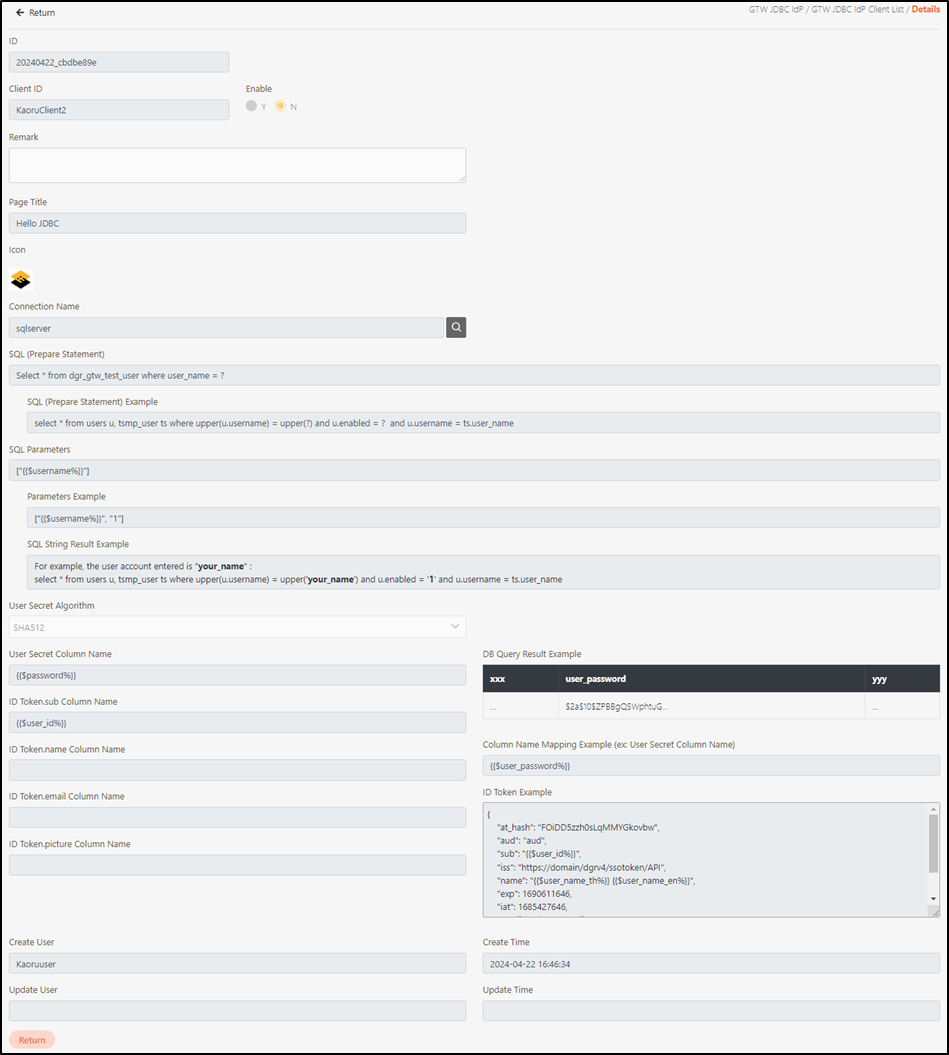
Access and view the JDBC IdP client details.
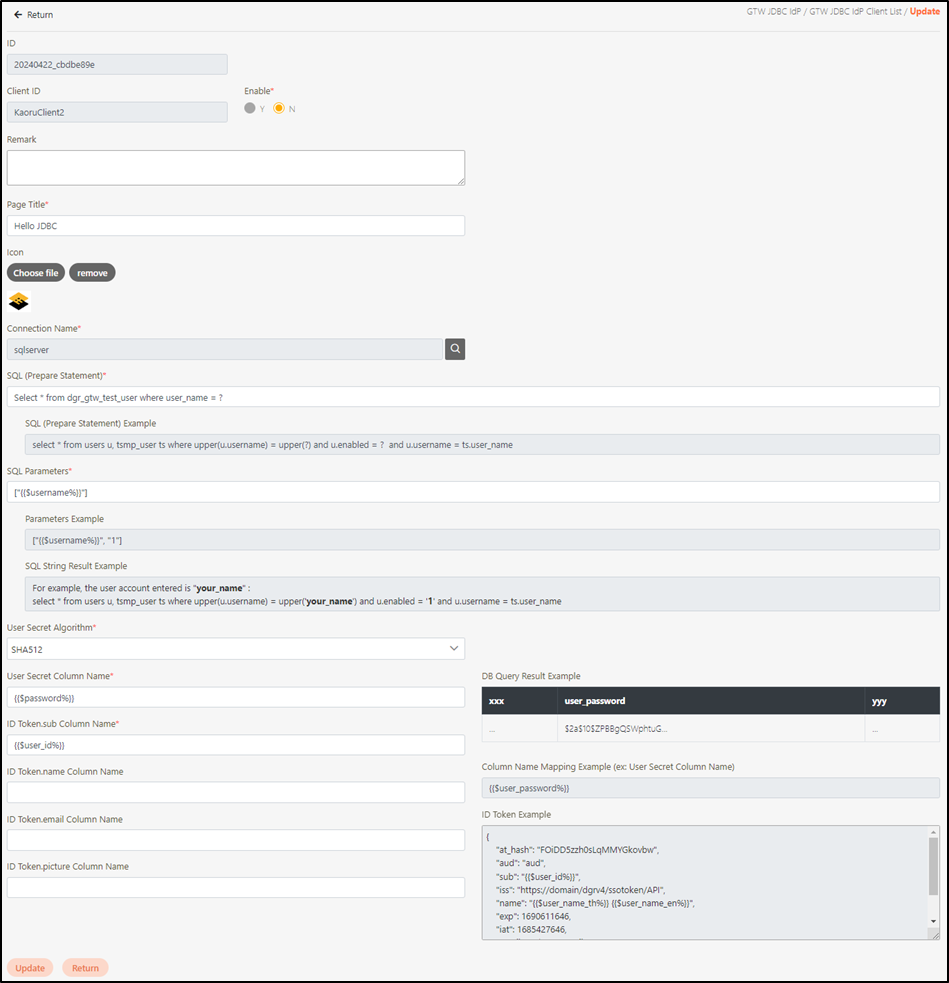
To update an JDBC IdP Client, search for the client you want to modify, and click on the
 icon to access the Update page.
icon to access the Update page.
Modify the desired fields, and click Update to save and exit.
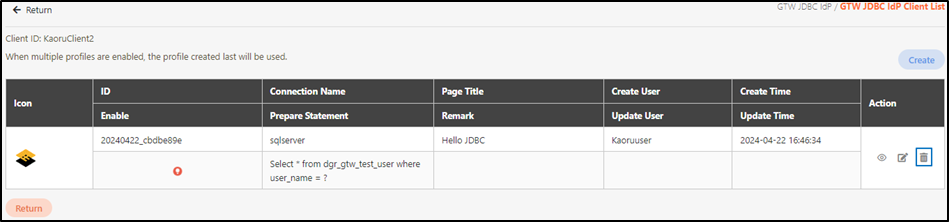
Select the client ID to delete, and click on the
 icon to proceed.
icon to proceed.
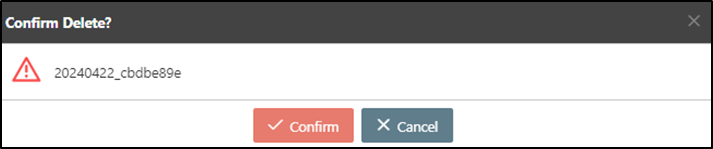
A warning prompt displaying the message “Confirm Delete?” will pop up. Click Confirm to delete this JDBC IdP Client and exit.
Last updated
Was this helpful?
